Unix Signals: Difference between revisions
pc>Yuron No edit summary |
m 1 revision imported |
(No difference)
| |
Revision as of 10:22, 9 August 2019
| On path: IPC | 1: Processes • 2: Interprocess Communication • 3: Shared Memory • 4: Files • 5: Unix Signals • 6: Pipes • 7: Sockets • 8: Synchronisation • 9: Synchronisation Barrier • 10: Atomicity • 11: Mutual exclusion • 12: Signal and Wait |
|---|
| On path: Exceptions | 1: Exceptions • 2: Reset • 3: System Calls • 4: Software Exceptions • 5: Emulator traps • 6: Memory Fault • 7: Interrupts • 8: Unix Signals |
|---|
| Depends on | Exceptions |
|---|
Beware: “signal” is used confusingly for somewhat different actions. This article is about signals which are a sort of software-level exception – such as the user pressing ^C. For the start-stop interprocess communications signals, try here.
Signals allow the operating system to notify a program when events happen. They can be used these to synchronise programs or to allow detection of errors. We can set programs up to perform different operations when catching different types of signals. Some signals Linux sends are below. Run man 7 signal for more.
SIGINTis received when the user performs a keyboard interruptSIGSEGVis received when the program attempts to access invalid memorySIGKILLis received when the program is being forcibly killed by the OS
The figure below tries to capture the relationship of the hardware-level exceptions (including system calls) and the SIGnals to the application processes.
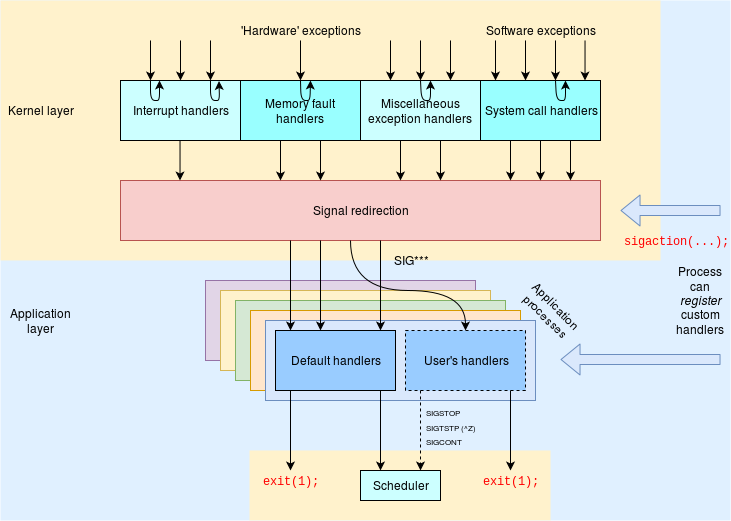
Many hardware interrupts are handled by their own device drivers; occasionally an interrupt will initiate a signal. Memory faults will typically be handled by paging or used to update internal kernel state – but sometimes will be genuine segmentation violations. Whilst most system calls are for services for the same process, several are able to send SIGnals as interprocess communications, particularly between parents and children.
The kill program is used to send signals to programs. “kill” is a misleading name; although it can be used to send ‘kill’ signals it can also send other signals. Check its man page to find a list of signals it can send, or see the POSIX signals in Wikipedia.
See also:
- All about Linux signals
man 7 signal- overview of Linux’s signals and their usesman 3 signalandman 3 sigaction- using signals in C programs
Practical
There is a practical introduction to handling Unix signals here.
| Also refer to: | Operating System Concepts, 10th Edition: Chapter 4.6.2, pages 188-190 |
|---|