Pointers
| On path: Pointers | 1: Memory • 2: Arrays • 3: Pointers • 4: Pointer Exercise • 5: Structures • 6: Dynamic Memory Allocation • 7: Malloc Exercise • 8: Structs Exercise |
|---|
| Depends on | Memory |
|---|
It is strongly recommended that you find a pen and paper before reading this page (and the subsequent exercises) for the first time. Pointers are clearer if you draw them.
An ‘int’ is a variable which holds a (integer) number.
A ‘pointer’ is a variable which holds an address.
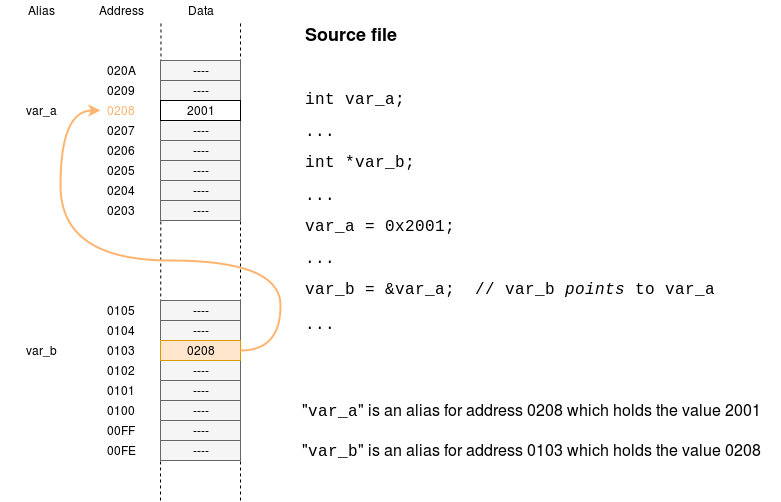
The figure shows a couple of fragments of a memory. The compiler/linker has assigned the two variables to particular locations (rather randomly in this case). The names become convenient aliases for the addresses of these locations.
In C we can find the addresses of variables although the actual value is not very useful; we can print it out – which is a bit interesting; we can store that address as ‘data’ in pointer variables of their own.
If you’ve got that scrap paper now, try this C exercise to explore what your machine/compiler are doing.
Although pointers are not exclusive to operating systems – most programs use them a lot – an appreciation of their operation is important because they are used extensively in structures such as linked lists.
In fact, you will have used pointers already (in Java) but there they are not as explicit.
Pointer values
Although it is possible to assign any value to a pointer it is likely that dereferencing a random value will cause problems. A program will only be permitted access to a limited part of the memory space by the operating system. By all means try it out: you’ll soon discover some segmentation faults.
There is one reserved address in C which is called NULL (it has a ‘numeric’ equivalent value too but that is really irrelevant). It can be used to say ‘this pointer goes nowhere’ and dereferencing it will result in a segmentation
fault.
If you establish the address of something which does exist in your program – such as by using the & operator – it is usually possible to use pointer arithmetic or array addressing to dereference ‘nearby’ values too. This can allow you to deduce something about how the compiler works etc. but it is hard work to make progress.
Don’t experiment with this unless you are a bit of a masochist!