Superuser: Difference between revisions
pc>Yuron No edit summary |
m (1 revision imported) |
(No difference)
| |
Revision as of 12:46, 26 July 2019
| On path: User |
|---|
| Depends on | User • Security |
|---|
Known by different names in different systems the superuser (root, admin, administrator) is able to obtain privileges not available to ordinary users. These typically include running processes in privileged mode(s) and the ability to modify features such as file permissions.
One user identifier (UID) is used to identify the “superuser”. A superuser can ‘become’ any other user, reset password entries etc.
Because the superuser can do anything – possibly inadvertently – it is not usually a good idea to assume this privilege except when necessary.
Note that superuser is not the same as a privileged mode in the hardware: it is a software privilege. A superuser’s applications will normally run (most of the time) in an unprivileged (“user”) hardware mode. When servicing exceptions, such as system calls, the hardware privilege will be raised (to allow access to hardware peripherals, protected memory etc. but the process will still be owned by its original user.
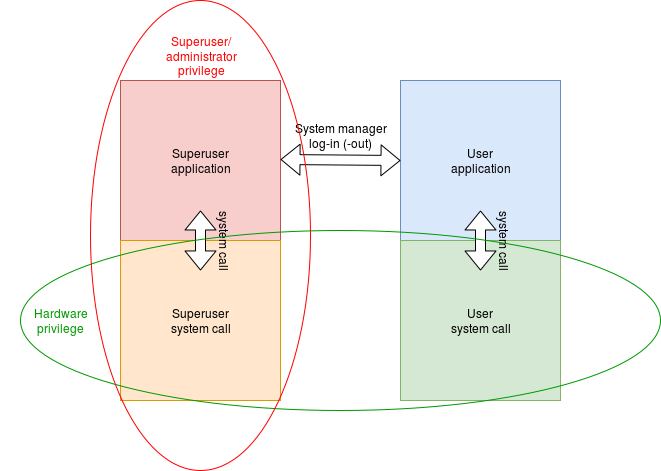
In practice there need not be much difference between the superuser
and other user privileges. For example, the Unix superuser
(“root”) can allow or forbid access to a particular
hardware port because (s)he owns the corresponding
‘file’ (in /dev/) and can thus change the ‘file
permissions’; other users cannot. There are a few calls which
are only allowed by root though – perhaps most notably the abilities
to change UID and change the ownership of a file/resource.