Containers
| Depends on | Security • Processes • Virtual Machines |
|---|
“Containers” is a generic term for virtual computers formed within a host system. This form of virtualisation is used to “contain” access for some users or processes to using certain sets of files or devices. In particular, if a server machine is notionally running many copies of the same operating system, containers can be used to make it look like many different (virtual) machines whilst the hardware and the operating system code is shared.
The container therefore looks like a virtual machine from the user perspective but does not require the expense of a separate kernel for each machine.
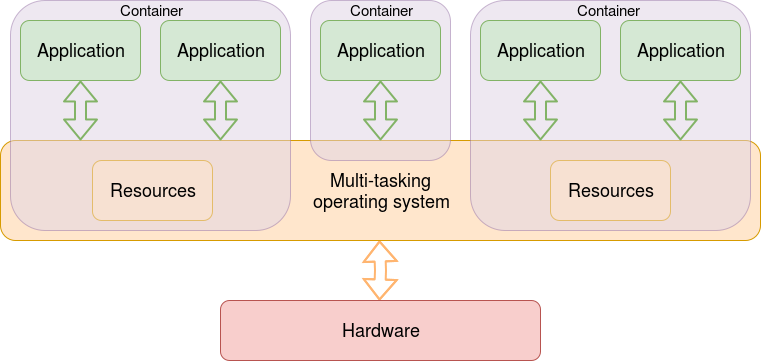
The container will probably have its own IP address and its own view of the filing system, in a manner like the earlier Unix chroot (see below) The apparent truncation of the file system is probably the most visible effect of the container for the user.
The container constrains its contents which provides some system security. It also provides (and encloses) the environment in which its contents run. This makes containers (potentially) more portable – including reducing the danger of things ceasing to work when some (apparently) remote set up is upgraded.
A container only needs to hold its own set of resources and processes. Being ‘lighter weight’ than a full-scale virtual machine it is easier (faster!) to port or copy. Thus a modern web-server might ‘contain’ each user, creating and destroying containers for the session.
Because different containers on the same physical machine are logically isolated they cannot communicate in ‘ordinary’ interprocess ways; they need to regard themselves as separate, networked computers – although they may be able to share files. The network software may be ‘clever’ enough to isolate the containers from the outside world, even if they are using (e.g.) IP to communicate. (NFS will allow computers to share file store across a network too, of course.)
Unlike a hypervisor-based system, all the containers must run under the same host O.S.
Docker
Docker is a major proponent of containerised software. Whilst it is not the purpose of this article to endorse any particular company there are some useful figures there.
chroot
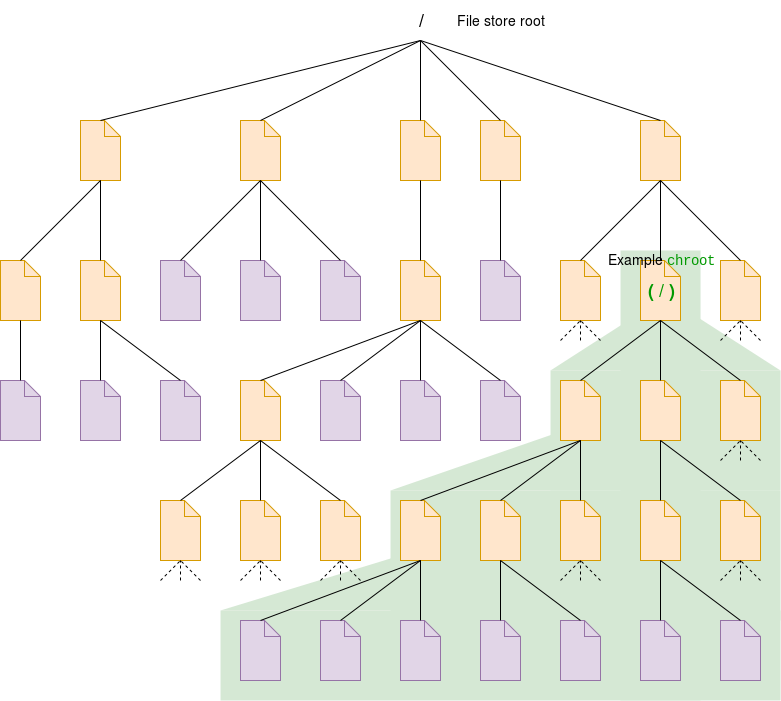
Although it does not provide complete “containerisation” the Unix chroot system call (only allowed to the root) will redefine the root (“/”) of the apparent file tree. This partial restriction can contribute to security, for instance by creating a “honeypot”.
However chroot (an old mechanism) alone cannot provide full security; a root user inside the subtree could mount another disk in its /dev/… or /proc/ to be able to see processes outside this space. It is more of a convenience than protection.
LXC
LinuX Containers (overview) are still fairly new, but liable to increase in prominence. (They are just one example; there are plenty of other approaches and the ‘standard’ is yet to settle out.)
Acknowledgement: Dr. Dave Gilbert: Red Hat Inc.
| Also refer to: | Operating System Concepts, 10th Edition: Chapter 18.5.8, pages 718-719 |
|---|